Introducing HackerOne Assets

Learn More About The Newest Addition To Our Evolving Attack Resistance Management Portfolio
Attack Resistance Management is the management of human security tests on your attack surface designed to increase your resistance to attackers. It is a cross-functional and continuous approach to improving security effectiveness and reducing risk.
While working with thousands of customers, we observed that digital transformations create an expanding attack surface, leaving gaps in most organizations’ security capabilities and processes.
To better understand and measure this gap, we surveyed over 800 security buyers across the U.S. and Europe and published our findings in The 2022 Attack Resistance Report. We asked about security practices, attack surface management, and how they understood their attack resistance. Of the organizations surveyed, only 63% believe their team can protect their attack surface. And nearly half of those surveyed lack confidence in their ability to address the risks introduced by this gap.
The Gap—Why Organzations’ Attack Resistance is Low
Organizations face shortcomings in four key areas: attack surface management, infrequent testing, inadequate security testing tools, and a security talent shortage. Combined, these create the attack resistance gap. Our survey found the latter two areas— inadequate tools and understaffed or unskilled security teams are the most severe issues. The four attack resistance gap components are shown in Figure 1 below.
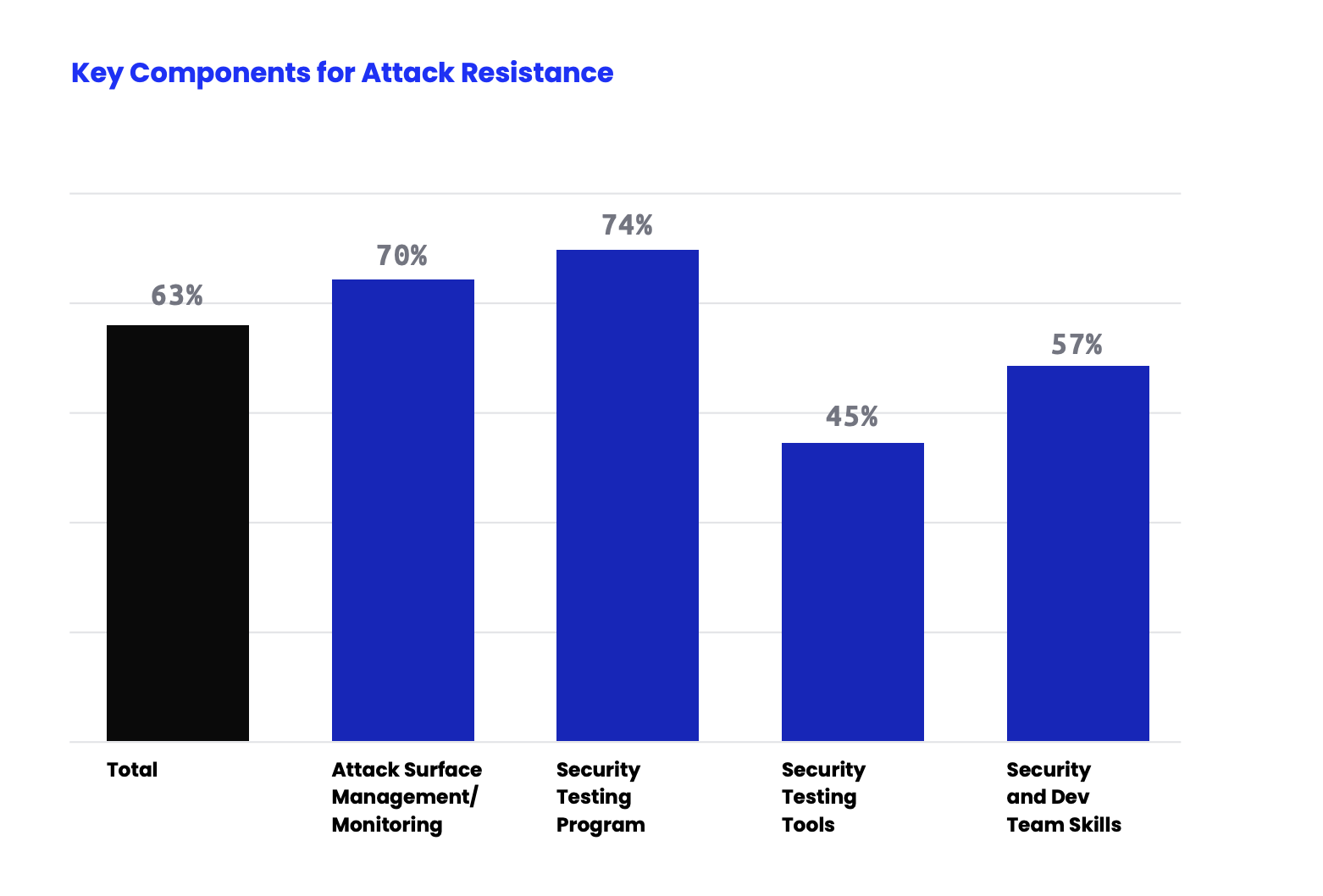
Incomplete Knowledge of Attack Surface: Organizations can’t defend what they don’t know about, and gaps in their attack surface make it impossible to assess risk accurately. In some ways, this is the most foundational of the four components. Many of the surveyed organizations scan their attack surface frequently—however, over 90% acknowledge they have blind spots. Questions that arise include: What assets are missing? How is the shape and size of your organization’s attack surface changing? How long is too long to have an unknown asset on your organization’s network? Answers to these questions are crucial and must be confirmed regularly.
Testing Frequency Does Not Keep Pace with App Updates: Continuous delivery and deployment are common practices. Your development team is likely to be pushing software updates weekly. It's intuitively insufficient to update production assets regularly and leave them untested, yet only one in three applications are tested more than once a year.
Shallow Scanning Tools: Automated scanning tools look for and reliably find common and well-known vulnerabilities. Scanners can be the fastest, cheapest, and most effective tool available in these cases. But scanners cant find vulnerabilities they’re not programmed to see—the unknown unknowns. Your organization needs the human ingenuity of ethical hackers to find a different class of vulnerabilities that no technology can. These are the most critical and complicated vulnerabilities that scanners miss.
Untested or Unavailable Skills: With an industry-wide talent shortage, hiring security talent that understands new technologies, not to mention custom APIs and legacy applications, is challenging. Your organization may have a strong security team, but development resources likely dwarf it. Keeping up is a challenge, leaving no time for offensive exercises or other proactive tests.
Close the Attack Resistance Gap with Continuous Improvement
One of the most important and successful ways to close your organization’s attack resistance gap is continuous team improvement. In the fourth component of the attack resistance gap, many organizations have untested or unavailable skills to meet their attack surface needs. They don’t have the time, money, or tools to invest in their teams. However, teams can’t increase testing frequency, learn new technologies, or update their threat models without these things, leaving organizations vulnerable.
Your development team will repeatedly make the same mistakes without skills improvement, thus reproducing vulnerabilities. And, your incident response team may not understand how to look for signs of weaknesses or evidence of an attack. These teams need continued education to keep their organization safe. Ultimately, this lack of investment leaves your organization struggling with the same issues across the board, creating inefficiencies and increased and unknown risk.
One major issue is that traditional developer education is unengaging, and applying generic teachings to your processes can be difficult. Your team will most likely prefer to write code than do training. HackerOne makes developer training relevant and interesting. We deliver better vulnerability intelligence by analyzing vulnerabilities from your codebase and feeding findings back into your development process. We can also provide custom scanner rules based on hacker findings and benchmark your organization against others in the same industry or using similar tech stacks.
What's New at HackerOne?
Attack Resistance Management is the culmination of years of work at HackerOne, building services, products, and integrations. Along with a global hacker community of over one million, we help customers improve security, mitigate risk, and close their attack resistance gap.
At the core of Attack Resistance Management is HackerOne Assets, our new attack surface management (ASM) product. HackerOne Assets is designed to address the first component of the gap—managing your entire attack surface. Many ASM solutions have the same shortcomings that scanning tools do—they cover a wide area but lack context and nuanced understanding. HackerOne Assets puts hackers' eyes on your assets, using the same recon skills they bring to bug bounty programs and pentest engagements. Because hackers are skilled at finding existing flaws, they also understand which are potentially vulnerable assets.
HackerOne Assets goes beyond other ASM tools by combining the strengths of hackers with comprehensive scan data. With your organization’s assets fully inventoried and risk-ranked, they can be added to the scope of your testing or bug bounty program. In addition, HackerOne Assets will support importing scan data from leading ASM products.
We have also added code review to our offerings with our acquisition of PullRequest.They offer on-demand reviews by vetted developers who understand software development and security. It's one of the best ways to find vulnerabilities in your pre-production code and provide direct feedback to your development team, helping them identify common errors and patterns.
HackerOne and Attack Resistance Management—How We Can Help
Fixing vulnerabilities is reactive. The goal is to create fewer vulnerabilities from the start and close the existing security gap, using continuous process improvement and ongoing education. Attack Resistance Management and the HackerOne Platform create a feedback loop between your vulnerability findings and development processes, building a stronger team, better processes, and higher-quality software.
As HackerOne expands our Attack Resistance Management offerings, your team will get cyclical benefits from our products. Each Attack Resistance Management solution component reinforces the others: HackerOne Assets for attack surface management and finding problematic assets, HackerOne Bounty for incentivized testing, HackerOne Response for public vulnerability reporting, HackerOne Assessments and pentests for on-demand targeted testing, and HackerOne Code Review.
HackerOne can help answer this question: What is your organization’s attack resistance gap? It’s different in every organization. Some may have tools that don’t meet their needs, while others need increased testing for frequent app updates. You may have multiple issues that make up your gap. Once the gap is identified, HackerOne can then help you close that gap. Contact us to learn more.
The Ultimate Guide to Managing Ethical and Security Risks in AI
